ID-o-matic App - Table of Contents
Introduction – before you begin
Amazon
(AWS) Cognito Configuration
Google
(CGP) Identity Platform Configuration
Adding
the IDP user ID in your Customer view
Introduction – before you begin
The ID-o-matic app synchronizes the Shopify customer information with your IDP (Identity Provider) or CIAM (Customer Identity and Access Management) user data.
This app addresses the following use cases:
· Merchants selling services/subscriptions that require customer's login into an existing platform
· Merchants wanting to gather all customers information in a central system (IDP)
ID-o-matic supports the following IDP/CIAM:
· Amazon (AWS) Cognito
· Azure AD B2C
· Google (GCP) Identity Platform
· Okta Auth0
ID-o-matic is best used with Shopify New Customer Account as it will not require to maintain passwords.
The App synchronizes the following user attributes:
· Email address (login)
· Name (First name and Last name combined)
· Telephone
The synchronization happens when a new Customer is created in Shopify, and subsequently when that Customer is updated. The master record is the Shopify customer, meaning that the attribute changes are driven by Shopify, and replicated to the IDP, and not the other way around. The only exception is the case where the user (email) exists in the IDP, but not in the Shopify customers, then there is an option (Resynch) to create the customer in Shopify.
Any other attributes (ex. addresses) are not maintained in the IDP.
Once created, the IDP user will be in a ”forgot password” state.
The App supports: Create, Update, and optionally Delete operations.
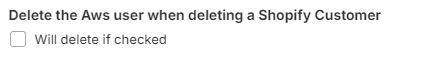
Delete is optional, but recommended to comply the Shopify Customer Redact (removal of personal information when a customer opts out of the Shopify store). However, there may be cases where it is required to keep the user in the IDP to continue the delivery of services. In the Admin panel, use this setting for deletion behavior (example for AWS):
Important: To configure ID-o-matic to work with your IDP, you will need adequate knowledge of the IDP you use, and access to its console, and some admin rights.
Amazon (AWS) Cognito Configuration
Gather all the information to connect to your AWS Cognito. You will need the User Pool Application client ID, the Access key and secret of an authorized user, and the region of your pool.
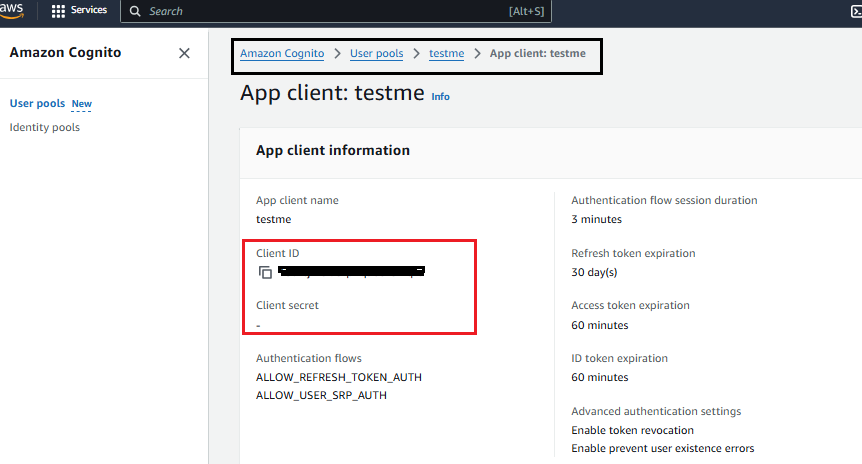
1.
Get you User Pool
Application client ID:
2.
Create an IAM policy
that contains the following permissions:
|
{
"Version":
"2012-10-17",
"Statement": [ {
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"cognito-idp:AdminDeleteUser",
"cognito-idp:AdminCreateUser",
"cognito-idp:AdminSetUserPassword",
"cognito-idp:AdminUpdateUserAttributes",
"cognito-idp:AdminGetUser",
"cognito-idp:AddCustomAttributes",
"cognito-idp:ListUserPoolClients",
"cognito-idp:ListUsers" ],
"Resource": "USER_POOL_ARN" }, {
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "cognito-idp:ListUserPools",
"Resource": "*" } ] } |
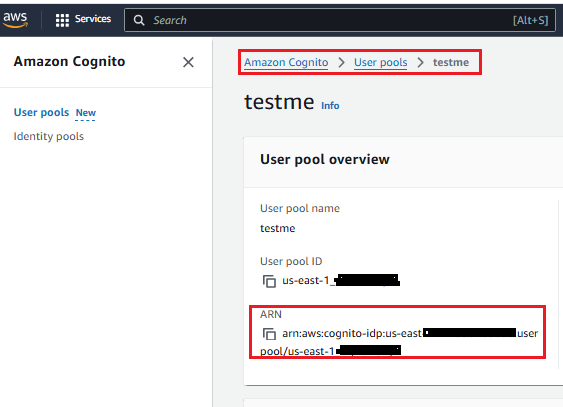
Replace USER_POOL_ARN with your
pool ARN – but leave the region open with a wild card “*” at the end, ex: "arn:aws:cognito-idp:us-east-1:XXXXXXXXXXXX:userpool/us-east-1_*")
You will find your pool ARN
here:
3.
Create an IAM user
with the attached policy above. The user does not need console access and
should not have any other permission.
4.
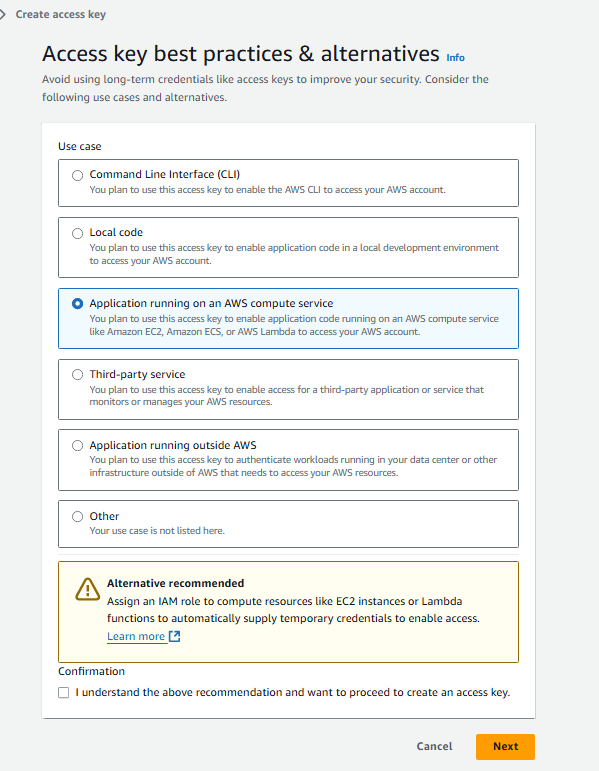
Create an access key
(choose “Application running on an AWS compute
service”) for this user. You will need this access key and secret for your
ID-o-matic configuration:
5.
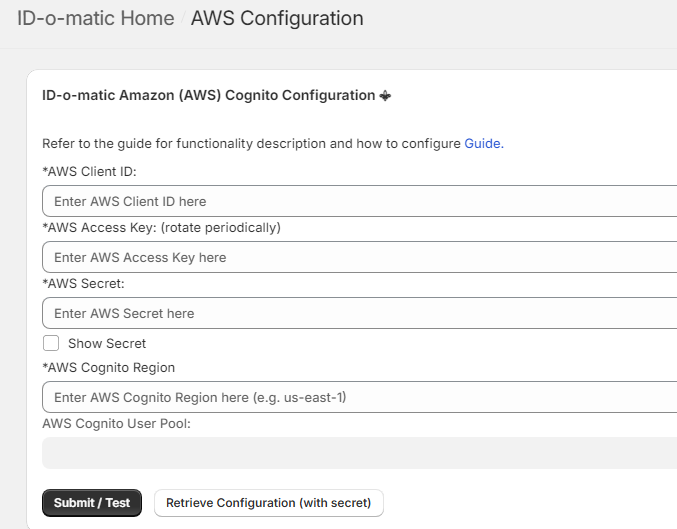
Enter all the information in the ID-o-matic
Admin panel (Amazon (AWS) Cognito Configuration page)
6.
Press “Submit /
Test” and your configuration will be tested and saved.
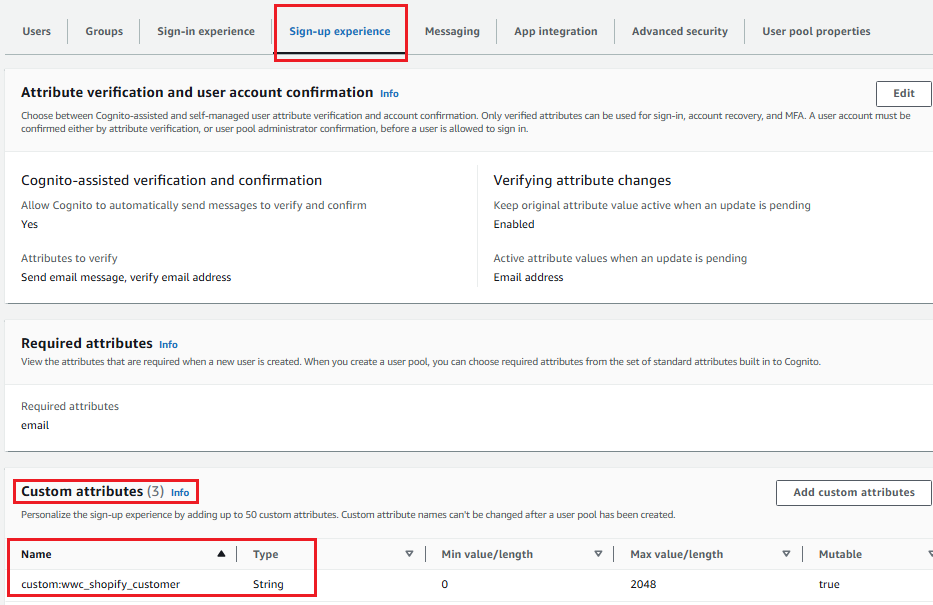
ID-o-matic will create this
custom attribute (wwc_shopify_customer) in your
Cognito User pool, this field will contain the Shopify Customer ID:
Azure AD B2C Configuration
Gather all the information to connect to your Azure AD B2C. You will need the Directory (Tenant) ID, The Application Client ID and secret.
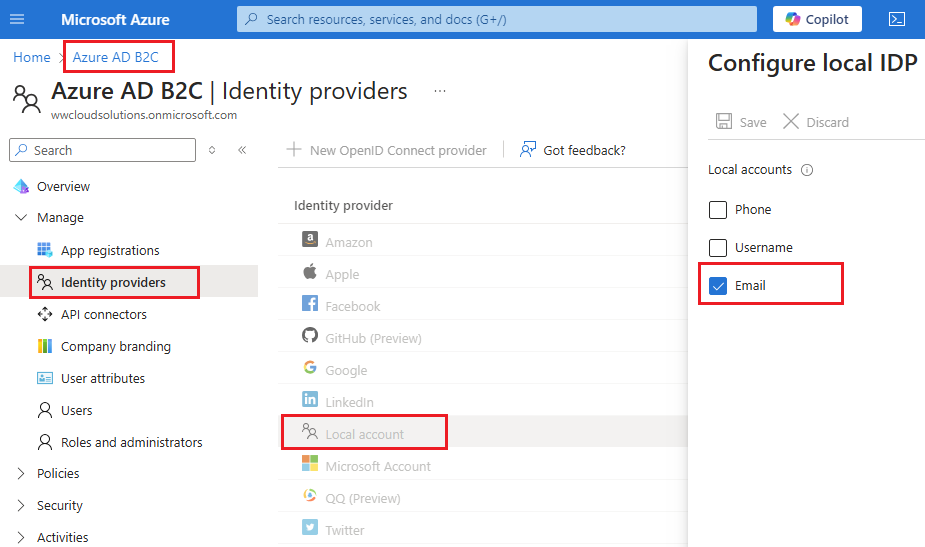
Important: ID-o-matic will work with email / Password provider, therefore make sure your Azure AD B2C “Local account” identity provider is set to email:
1.
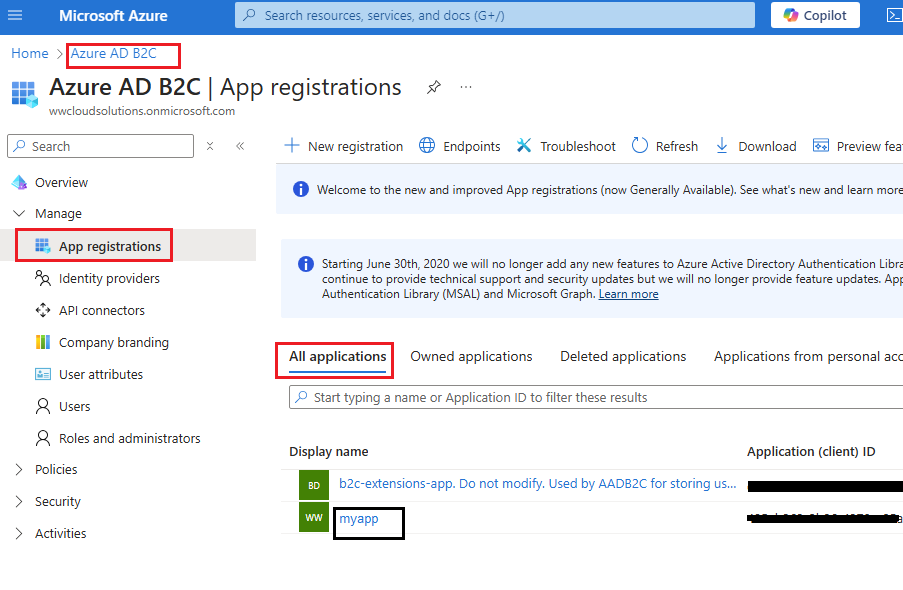
Go to the Azure AD
B2C , section App registrations, and select you
application (example):
2.
Get the Application Client ID, secret, and Tenant
ID:

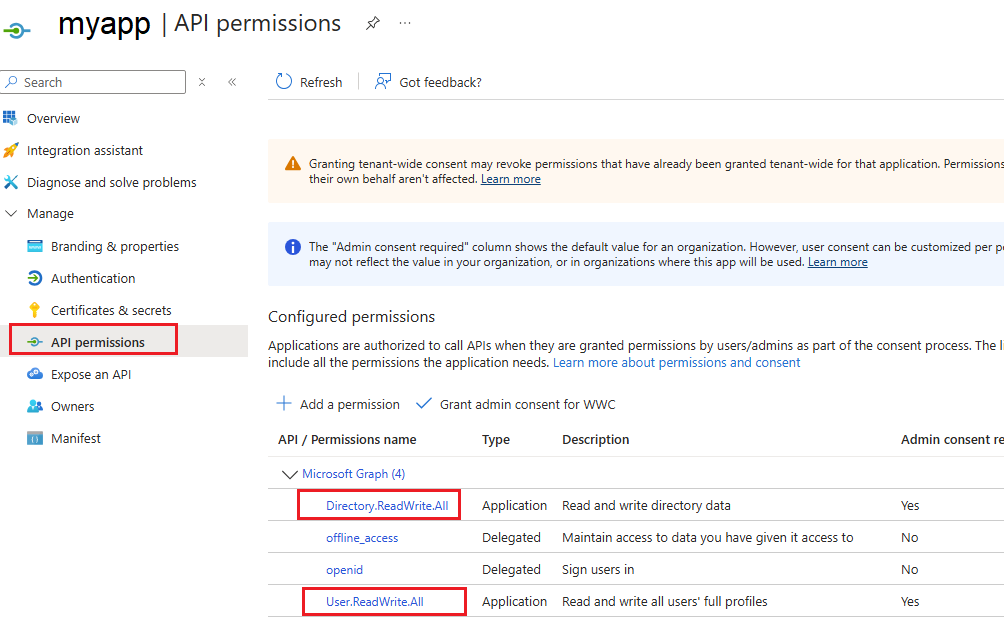
3.
Go to the API
permissions section, and add the following permissions: Directory.ReadWrite.All, User.ReadWrite.All:
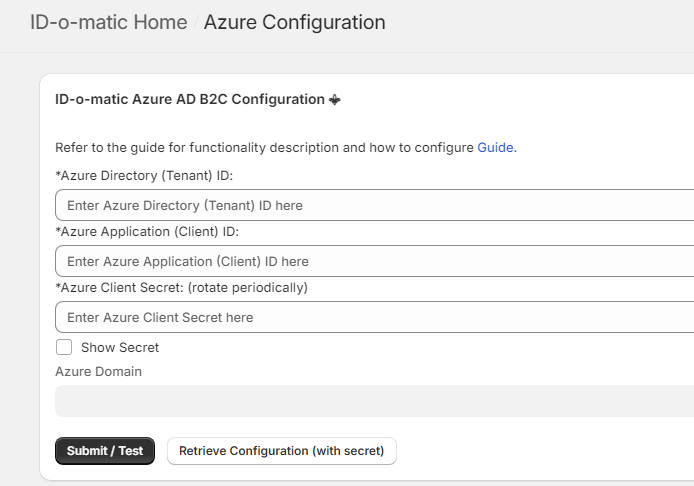
4.
Enter all the
information in the ID-o-matic Admin panel (Azure AD B2C Configuration page):
5.
Press “Submit /
Test” and your configuration will be tested and saved.
Although not readily visible in your Azure console,
behind the scene, this extension attribute is added to Azure B2C users: extension_(your
client ID without hyphens)_shopCustumer. This attribute
will contain the Shopify Customer ID.
Google (CGP) Identity Platform Configuration
To configure Google Identity Platform in ID-o-matic, you will need a json file generated in Google Identity Platform console.
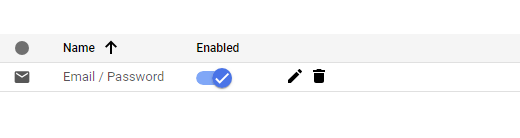
Important: ID-o-matic will work with email / Password provider, therefore make sure you project / application has this provider enabled for you identity Platform project:
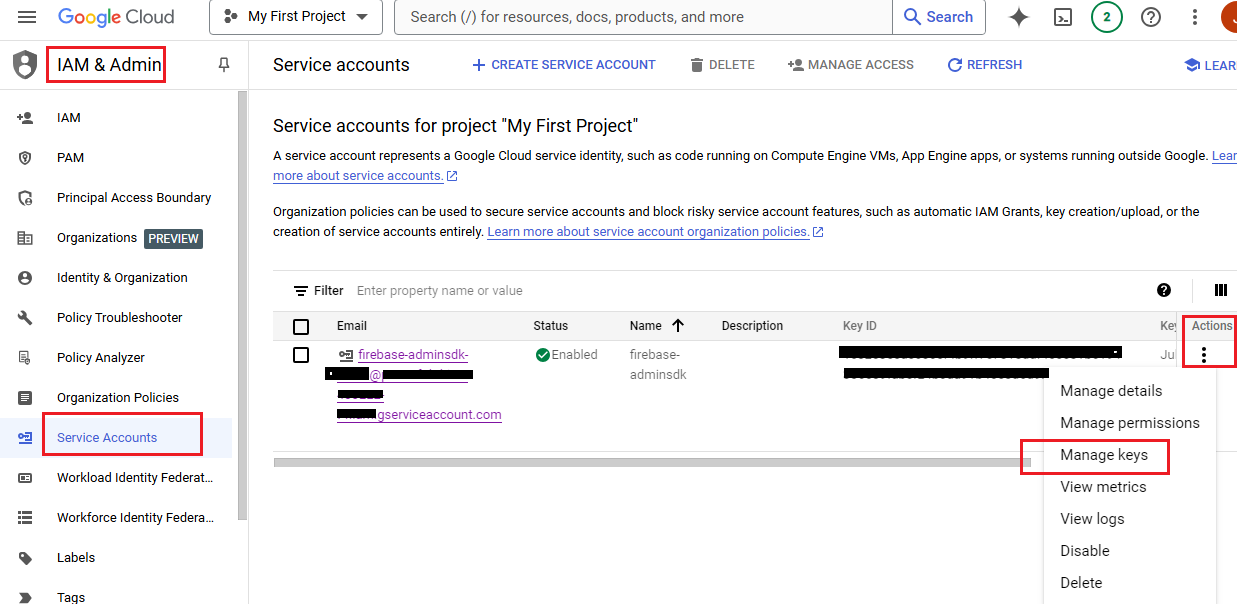
1.
In the IAM &
Admin menu, select Service accounts and choose your Firebase Admin user (of
your Firebase project), then go to Manage keys:
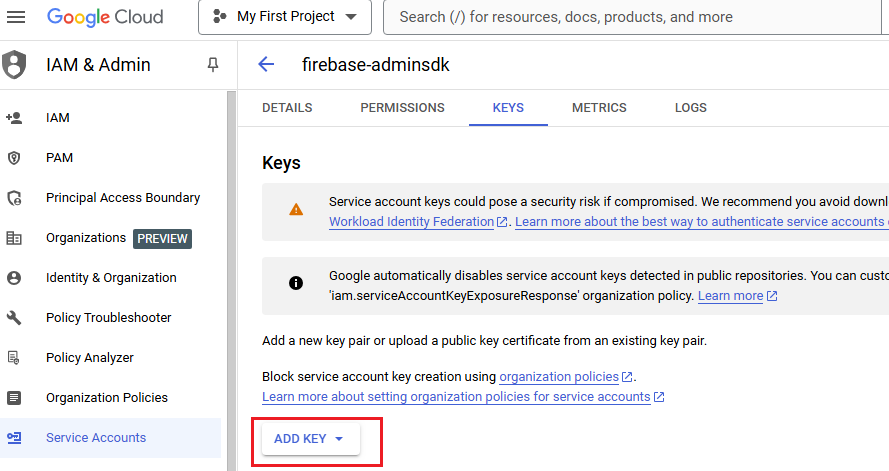
2.
From there, you can generate a json file containing the identity Platform
information and credentials:
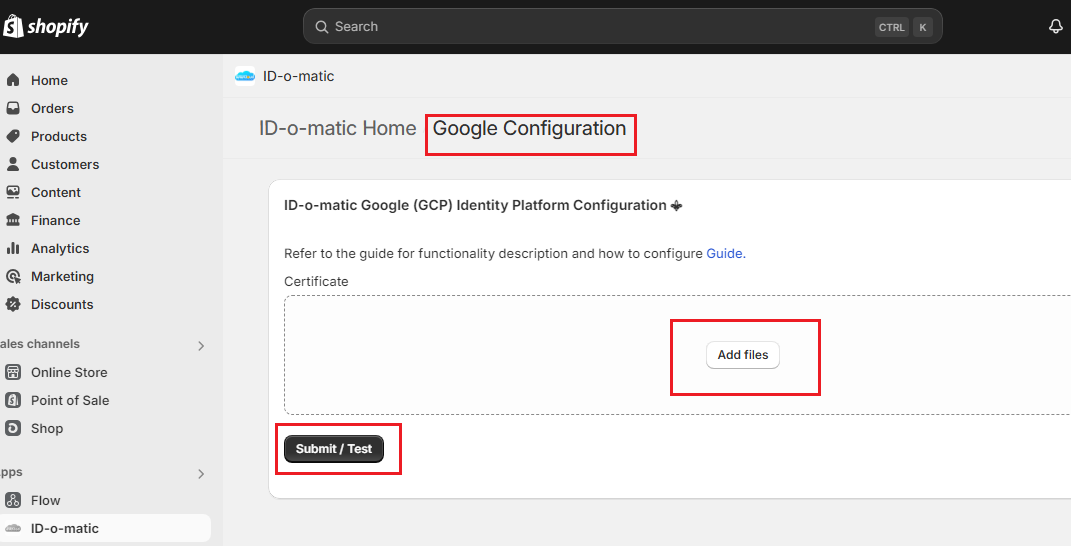
3.
Load the json file into the ID-o-matic Admin panel (Google (GCP
Identity Platform Configuration page):
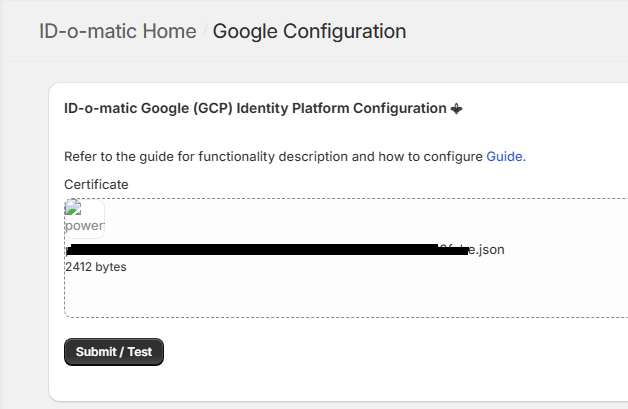
4.
Press “Submit /
Test” and your configuration will be tested and saved.
Although not readily visible in your Google console,
behind the scene, this custom attribute is added to Google
Identity Platform users: wwc_shopify_customer. This attribute will contain the
Shopify Customer ID.
Okta Auth0 Configuration
ID-o-matic is compatible with Okta Username-Password-Authentication (Database) connection type.
To configure Okta Auth0 in ID-o-matic, you will need to create a web app, and obtain the Tenant ID, the Tenant Location, and the application Client ID, and secret from the Okta console.
1.
Create a Regular Web
Application and obtain Client ID, and secret:
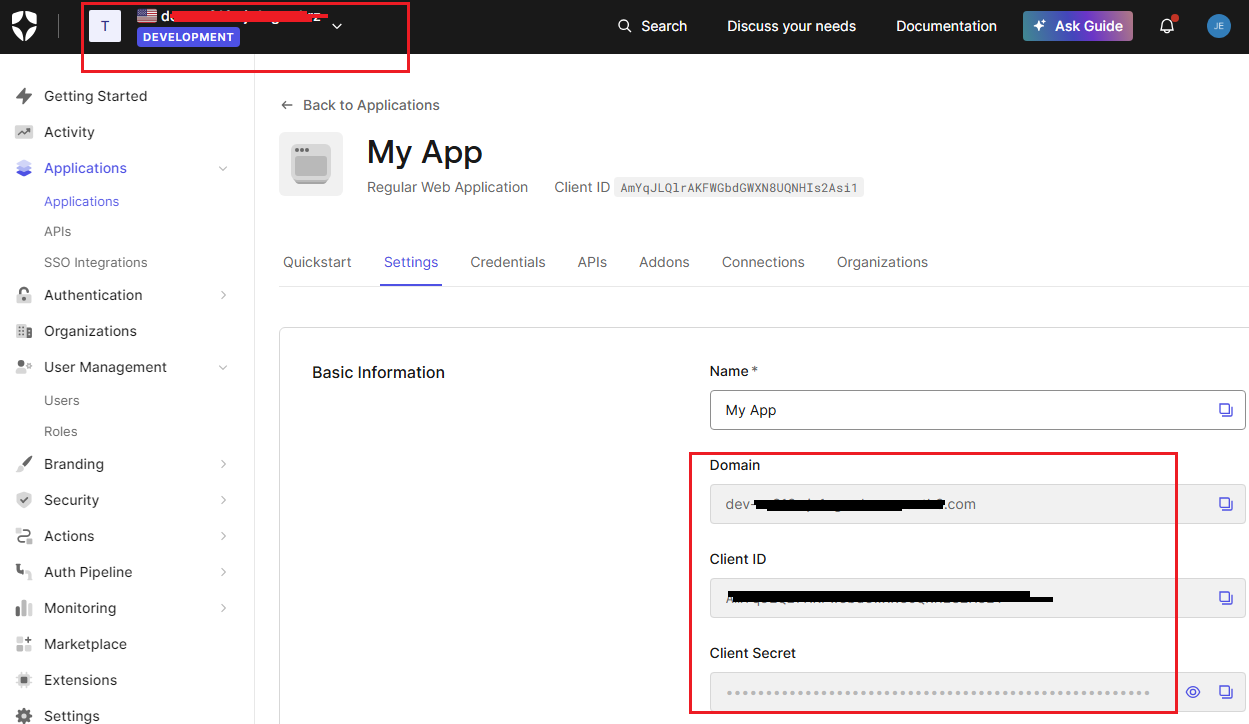
The Tenant ID can be obtained
from the top left of the console (or the Application Domain
without the “.us.auth0.com”). Above, the Tenant Location is in
the Application Domain, ex “us” if domain ends with “.us.auth0.com”.
2.
Make sure the
Application has Username-Password-Authentication (Database) connection enabled:
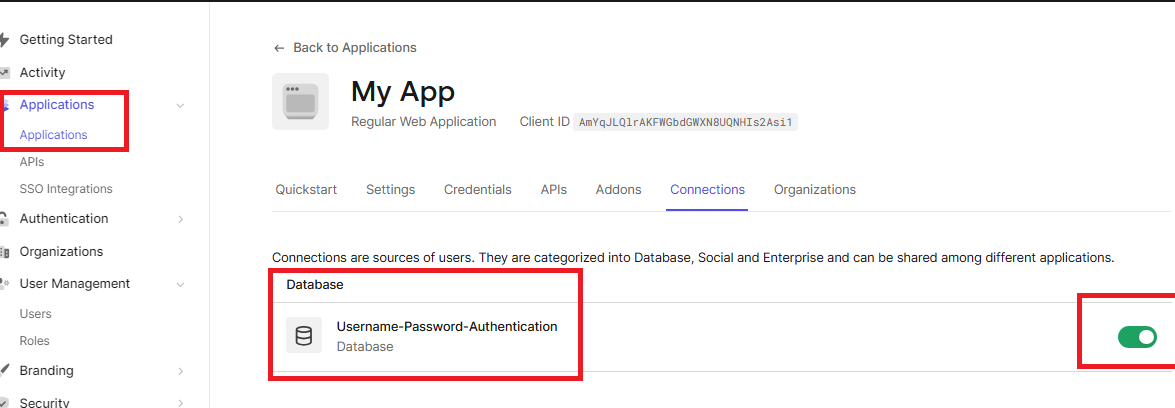
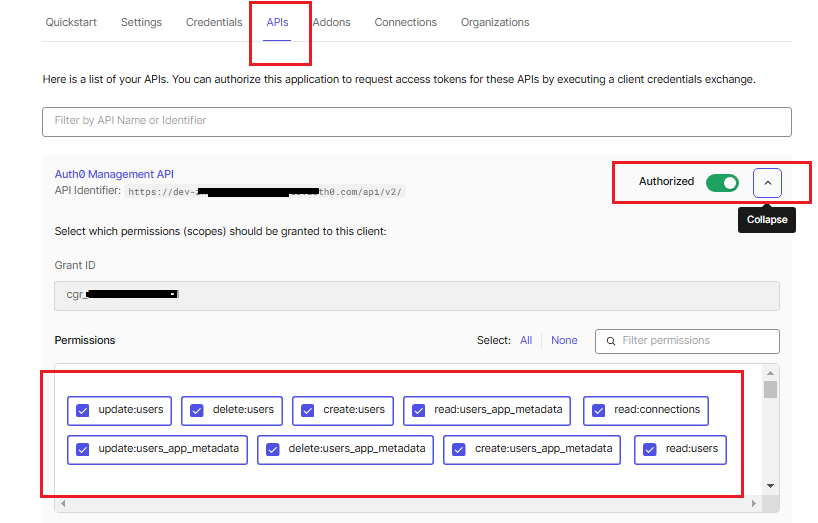
3.
The Application must
have the API authorized, with the following 9 permissions:
4.
Enter all the
information in the ID-o-matic Admin panel (Okta Auth0 Configuration page):
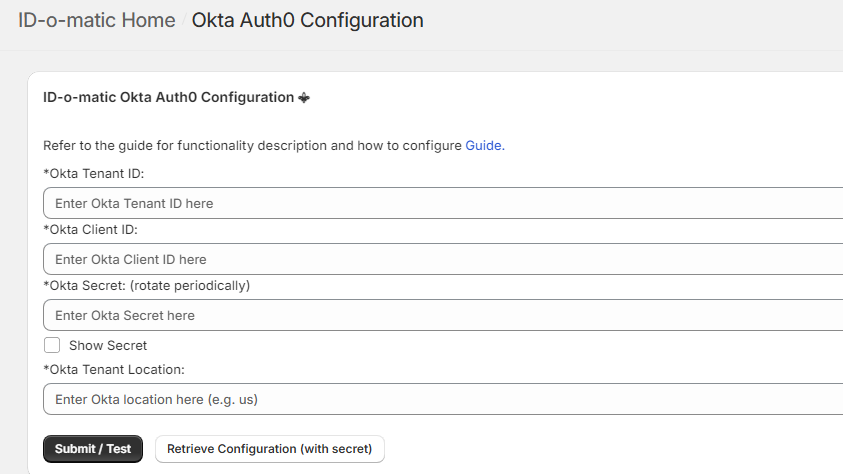
5.
Press “Submit /
Test” and your configuration will be tested and saved.
For each Shopify customer created, these 2 custom
attributes are added to the Okta user: wwc_shopify_customer (containing the Shopify Customer ID) and
wwc_phone_number (containing the Shopify Customer
phone number, if provided). These can be viewed in the user’s Raw JSON section:
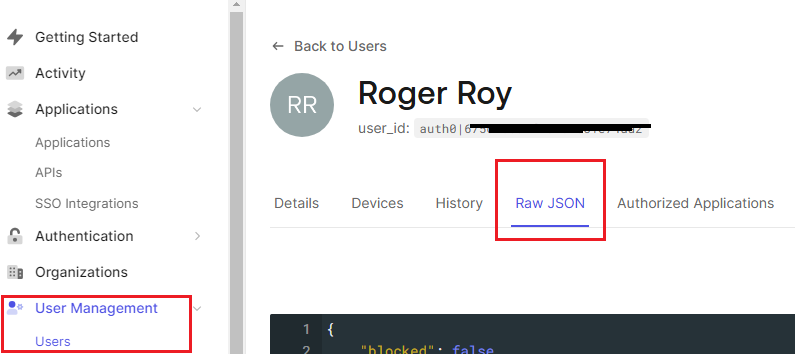
Test your configuration
Create a dummy customer in
Shopify:
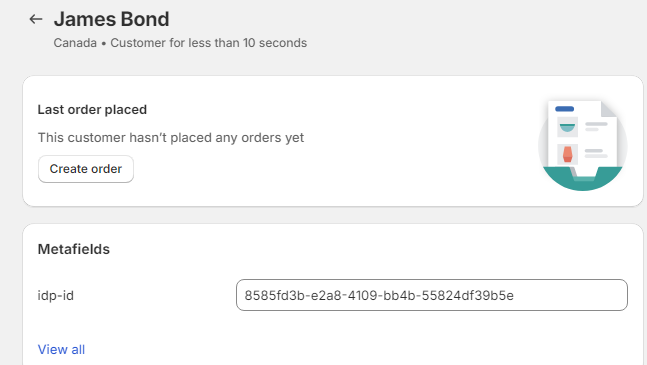
Once created in Shopify, you
should see the IDP user ID (idp-id) in the metafields section (refer to section Adding the IDP user ID in
your Customer view for setting up
unstructured metafields):
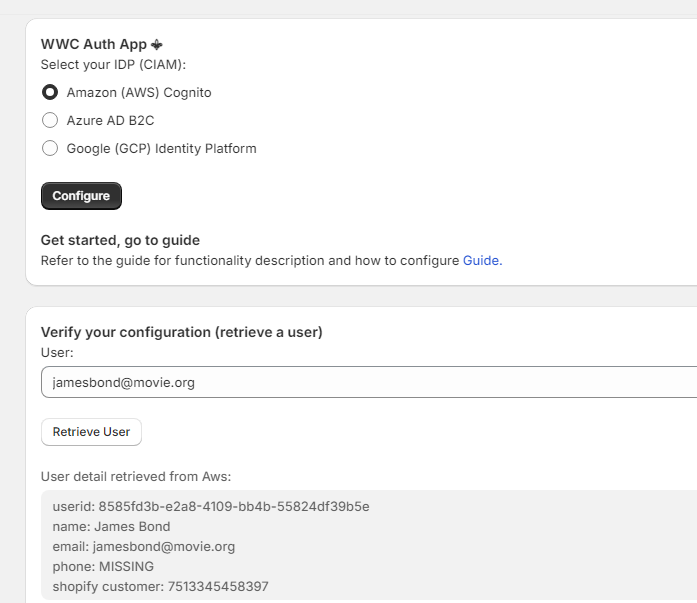
You should also be able to
retrieve it from the admin panel:
Security
Credentials to the IDP are required to create, modify and delete users.
The credentials are encrypted and kept in a secured database and cannot be accessed by anyone. Yet it is highly recommended that you rotate the credentials on a regular basis.
You will receive a warning when your credentials are older than 90 days:
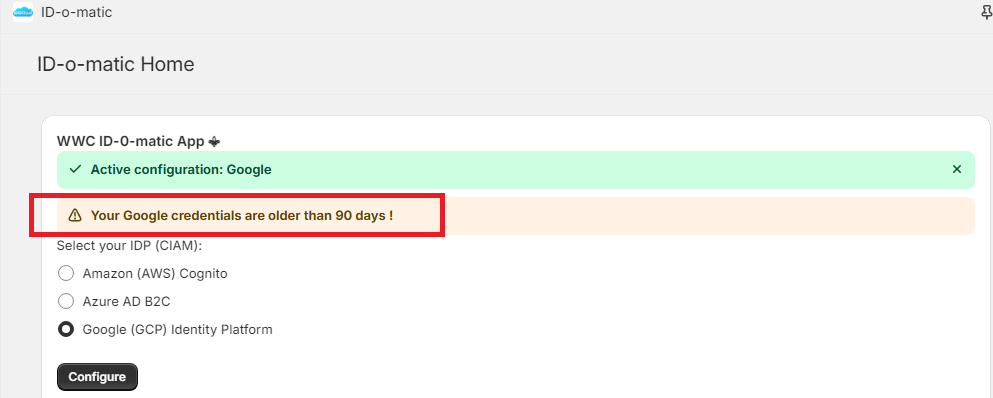
You can retrieve the current configuration (and credentials) by entering your old secret (example here Amazon Cognito):
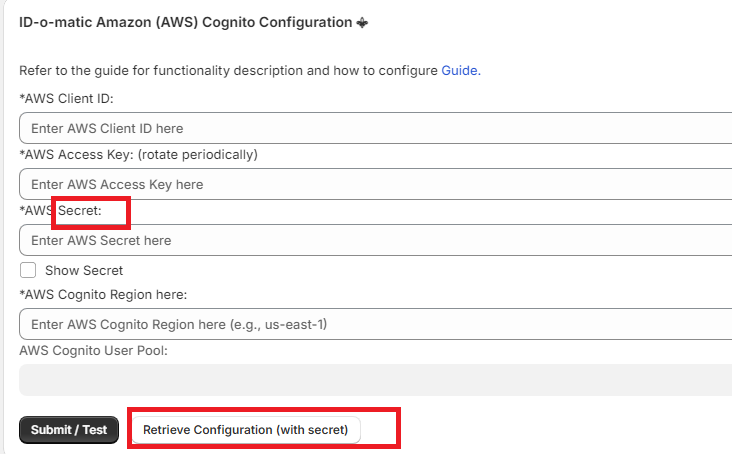
Then enter the newly generated credentials and Submit / Test. NB: for Google Identity Platform, simply generate a new json file and reload it.
Make sure to delete the old credentials (key or secret) in your IDP console once successfully re-entered in ID-o-matic.
The application requires read/write privileges for your Shop customers: read_customers, write_customers (the app will request those upon installation).
The application will also create a Customer metafield, named “wwc.sub” (see Adding the IDP user ID in your Customer view) that will be saved along with your customer data.
Adding the IDP user ID in your Customer view
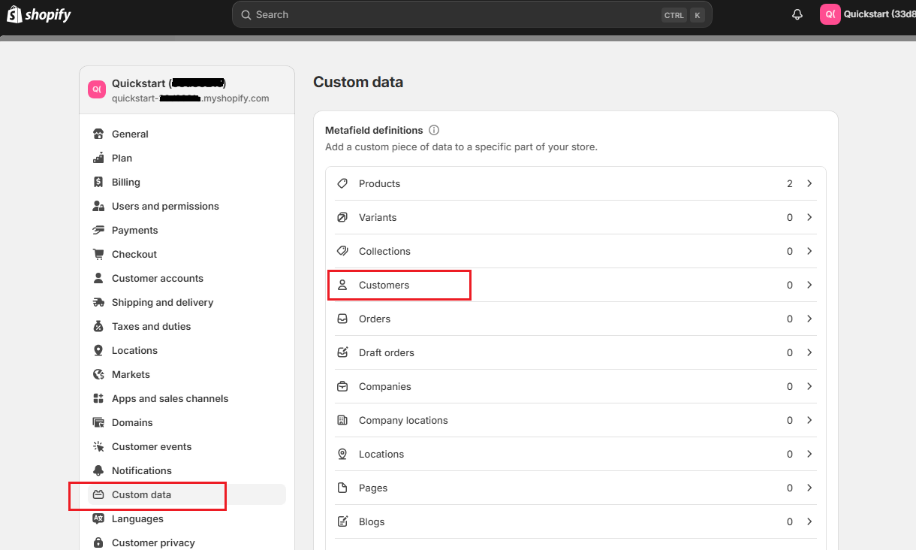
Optionally, you can add custom data field (Customer metafield definition) in your shop, so that the IDP user ID can be displayed in your Customer page.
1.
Go to your shop
setting, and navigate to custom data for customers:
2.
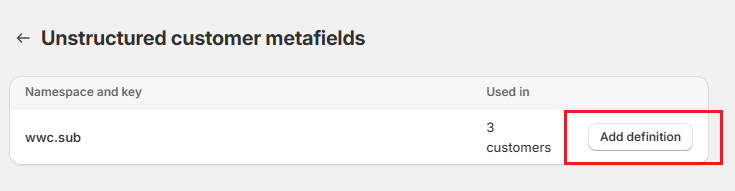
Select unstructured metafields:
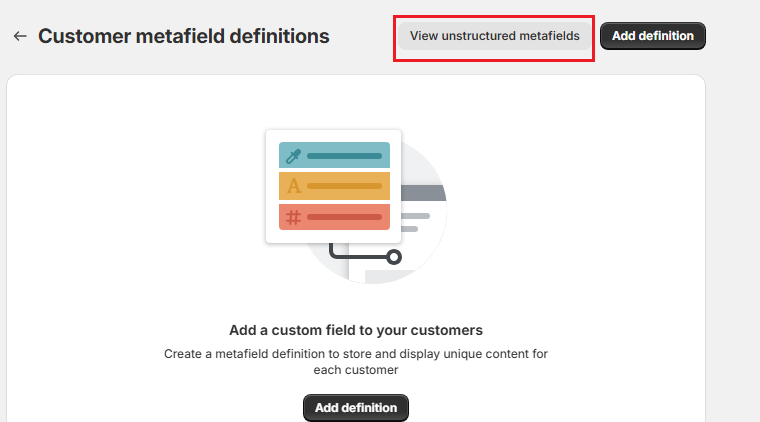
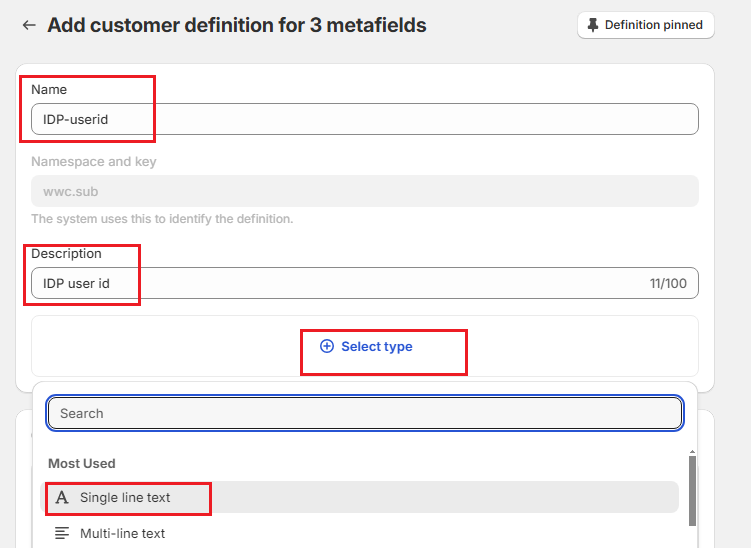
Pick “wwc.sub”
and add a definition, and save:
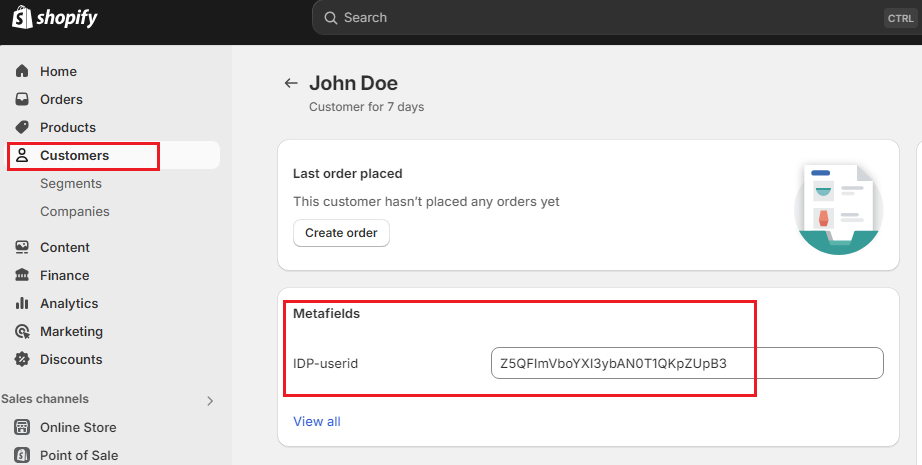
As a result, you will now see
the IDP user ID in the Customer page:
Troubleshooting
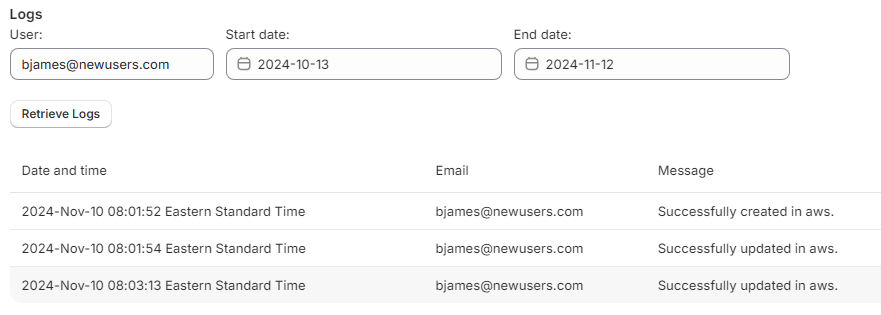
You can use the Logs section in
the Admin panel to retrieve the actions on users. You can specify a specific user (email) or leave
blank for all users, and specify a range of dates:
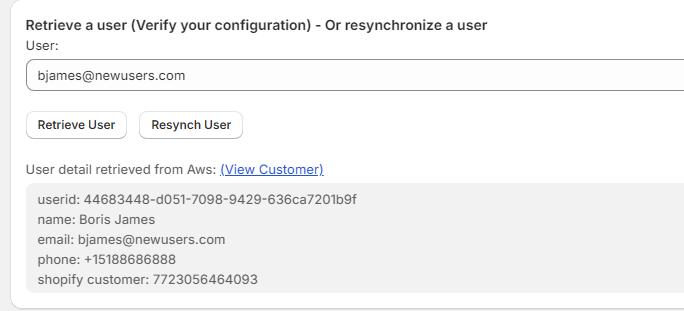
You can verify the status of a
IDP user, with the Retrieve a user section of the Admin
panel:
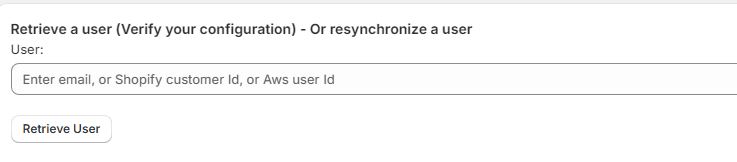
From there, you will be able to
resynchronize a customer if the data in the IDP differs from the data of the
Shopify customer (email, name, or phone). Thus, the Resynch button will update
the IDP user from the Shopify Customer data. If no customer is present in
Shopify for a given IDP user (email), Resynch will create a Shopify customer.